- Account Home
- Language
- News
- Products
-
Cases
By Service
- Help & Support
- Partners & Training
- About Us
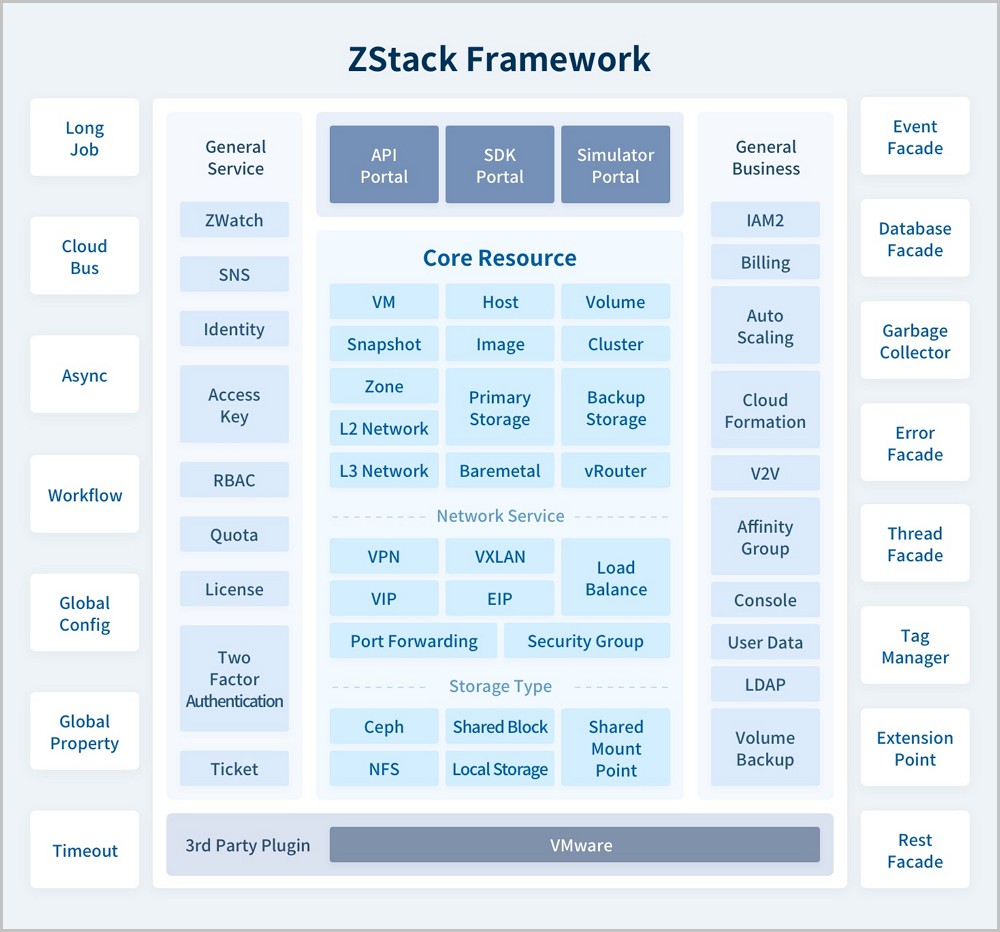
As a productionized private cloud, ZStack allows you to manage and schedule the compute, storage, network, and other resources in your data center. By using ZStack, you can quickly configure your private cloud environment, create VM instances, allocate volumes, and automatically configure the networks of the VM instances.
| Type | Feature | ZStack Enterprise |
|---|---|---|
| Zone | Multi-zone management |
|
| vCenter | vCenter management | Takes over multiple VMware vCenters via public APIs provided by VMware. In addition, highly compatible with and manipulates a portion of features of VMware vCenter Server to achieve unified managements of multiple virtualization platforms.
|
| vCenter multiple-tenant management | Tenants (normal accounts or project members) can manipulate the resources of the vCenter that you took over.
| |
| vCenter resource pool |
| |
| ESX VM instance |
| |
| Network |
| |
| Storage | Differentiates primary storages from backup storages according to datastore. | |
| Image | Allows you to manage the lifecycle of images, such as adding, deleting, enabling, and disabling an image. | |
| Host | Allows you to manage the lifecycle of hosts, such as placing a host in maintenance mode. | |
| Volume | Allows you to manage the lifecycle of volumes, such as creating, deleting, attaching, and detaching a volume. | |
| Real-time performance monitoring | Collects data of the ESX VM CPU, memory, storage, and network, and provides a visual, real-time display of these data in the UI. | |
| Cluster | Storage infrastructure | Uses homogeneous storage services within clusters, allows you to attach storage services to the clusters, and provides high availability features for VM instances. |
| Host | Supports host managements within a cluster. For a host, provides real-time display of all CPU utilizations, all memory utilization percentages, all inbound and outbound speeds of NICs, and all write or read IOPS. | |
| VM instance | Supports VM managements within a cluster. For a VM instance, provides real-time display of all CPU utilizations, all memory utilization percentages, all inbound and outbound speeds of NICs, and all write or read IOPS. | |
| Cluster functionality |
| |
| Network service |
| |
| Distributed resource scheduler (DRS) | Monitors and manages CPUs or memory workloads of hosts by cluster, and offers scheduling suggestions according to the configured scheduling strategies. You can manually migrate VM instances according to the scheduling suggestions to effectively improve your cloud stability while balancing cluster workloads. | |
| Advanced settings | Configures parameters for cluster resources by cluster:
| |
| Host | Virtualization | Supports KVM and VMware virtualization technologies. |
| Custom ISO | ZStack Custom ISO has two versions: c76 ISO and c74 ISO.
| |
| Resource overcommitment settings | Allows you to set overcommitment ratios for CPUs, memories, and primary storages to meet different resource usage requirements in cloud environments. | |
| Nested virtualization | Supports KVM or ESXi nested virtualizations. You can enable CPU hardware virtualization within VM instances. | |
| Real-time monitoring | Collects data of the host CPU, memory, disk I/O, disk capacity, and associated network, and provides a visual, real-time display of these data in the UI. | |
| Disable and enable |
| |
| Maintenance mode |
| |
| Physical GPU passthrough | Entirely passes through all peripheral devices (GPU graphics cards, GPU sound cards, and other small devices on other GPUs) on physical GPU devices as a group to effectively improve high-performance compute and graphics processing capabilities. | |
| vGPU |
| |
| SR-IOV | Generates multiple VF NICs from a physical NIC based on the SR-IOV specification, and allocates these VF NICs to VM instances. This helps to use resources more flexibly, improve resource utilization, and save costs. | |
| PCI whitelist | Passes through any VT-D device, such as Ali-NPU card, IB card (PCI mode), and FPGA card, to VM instances according to a whitelist. | |
| USB passthrough |
| |
| Intel EPT hardware support | Allows you to disable the Intel EPT hardware support to effectively address the problem of VM creation failure due to the CPU models are too old. | |
| Encrypted password storing | Allows you to store encrypted passwords for hosts. | |
| Operation logs | Displays audit information associated with event login operations when you manage and operate hosts. | |
| CSV file exporting | Allows you to export host lists in CSV format to facilitate the statistics analysis of your hosts. | |
| VM instance | Batch operation | Manages VM instances in bulk. |
| VM instance creation |
| |
| VM lifecycle | Allows you to manage the lifecycle of VM instances, such as creating, stopping, booting, rebooting, powering off, deleting, pausing, and recovering VM instances. | |
| Online resizing for root volume | Allows you to resize the capacity for a VM root volume online to change VM configurations. | |
| Online resizing for data volume | Allows you to resize the capacity for a VM data volume online, which will take effect immediately after the resizing. | |
| VM console |
| |
| VM snapshot |
| |
| CPU binding | Binds a logical CPU of a VM instance to a physical CPU of a compute node. | |
| Online password changing | Allows you to change passwords online for Windows or Linux VM instances. | |
| Online image creation | Allows you to create images online for running VM instances. | |
| QGA switch | Flexibly controls and manages the state of the QEMU guest agent. | |
| RDP mode switch | For a VDI UI, opens consoles in RDP mode by default after the RDP switch is enabled. | |
| Graphics card changing | Provides multiple VM graphics card types, including QXL, Cirrus, and VGA. | |
| Graphics card passthrough | Passes through a NVIDIA GPU device or an AMD GPU device directly to a VM instance. | |
| User data importing | Allows you to import user data when you create a VM instance. | |
| VM cloning without data volume |
| |
| VM cloning with data volume |
| |
| Operating system changing | Allows you to change the operating system for a VM instance that is in the stopped state. | |
| VM resetting | Resets VM instances to their initial image state, and overwrites all data in root volumes. | |
| Root volume resizing | Allows you to resize a root volume of a VM instance that is running or stopped to change VM configurations. | |
| ISO-based deployment |
| |
| Template-based deployment | Creates VM instances based on system templates. | |
| BIOS mode |
| |
| VM image creation | Makes a template image based on the current VM instance so that you can create VM instances in bulk in a custom manner.
| |
| Custom MAC |
| |
| VM boot order | Adjusts VM boot orders to change the ISO boot mode. Currently, the following boot devices are supported: CD-ROM, hard disk, and network. | |
| Dynamically attaching or detaching volume | Allows you to dynamically attach a volume to or detach a volume from a VM instance, to optimize drive models, and to identify a volume by its SCSI WWN. | |
| Dynamically attaching or detaching NIC | Allows you to dynamically attach a NIC to or detach a NIC from a VM instance, and to set the default NIC. | |
| Dynamically attaching or detaching virtual drive | Allows you to dynamically attach a virtual drive to or detach a virtual drive from a VM instance, and attach ISOs to or detach ISOs from each virtual drive. This will meet your needs, enhance the flexibilities, and improve the user experience. | |
| Attaching GPU card | Allows you to attach a GPU device when you create a VM instance. | |
| Shared volume | For Ceph and Shared Block primary storages, multiple VM instances can share the same data volume. | |
| Real-time performance monitoring | Displays VM workloads in real time for popular systems, such as Linux, Windows, and Chinese domestic operating systems.
| |
| High availability(HA) | Automatically reboots a VM instance if its host encounters failures, and displays the rebooting process in the UI. | |
| Online changing for VM CPU or memory | Changes CPU or memory configurations online without rebooting a VM instance. | |
| Real-time update of volume QoS and network QoS | Allows you to set QoS for the root volume and NIC of a VM instance, avoiding that a single VM instance occupies too many resources. | |
| SSH key injection |
| |
| Custom instance offering | Allows you to customize an instance offering to meet the resource consumption requirements. | |
| Custom tag | Allows you to customize tags to meet the querying and compiling scheduler tasks. | |
| Custom VM list | Allows you to either customize display items of a VM list or to export the VM list in CSV format. | |
| Resource deleting protection | Moves deleted VM instances to a recycle bin, allowing you to recover or completely delete the VM instances as needed. | |
| Cold migration |
| |
| Online migration |
| |
| Storage migration |
| |
| Cross-cluster HA policy | Allows you to configure a cross-cluster HA policy for a VM instance or VPC vRouter. Then, the VM instance or VPC vRouter will be stuck to the cluster to which the VM instance or VPC vRouter belongs when the policy takes effect. | |
| Operation logs | Displays audit information that is associated to an operation process event and a login operation of a VM instance. | |
| Guest tools |
| |
| USB redirection | Redirects a USB device on a VDI client to a VM instance. | |
| CSV file exporting | Allows you to export a VM list in CSV format, which facilitates statistics analysis. | |
| Anti-spoofing |
| |
| VM priority |
| |
| VM multi-gateway | Allows you to enable multi-gateway by running zstack-cli. After enabled, each NIC has an independent gateway. | |
| NIC multiqueue | Allows you to set the number of queues when Virtio NIC traffics are allocated to multiple CPUs. This helps to improve the NIC performance. | |
| Setting VM NIC model | Allows you to set the NIC model for Linux and Paravirtualization VM instances. Supported NIC models include Virtio, E1000, and RTL8139. | |
| Setting hostname or password |
| |
| Advanced settings | Allows you to configure parameters for VM resources by VM instance.
| |
| Auto scaling group | Lifecycle management | Allows you to manipulate the lifecycle of auto scaling groups, including creating, enabling, disabling, and deleting an auto scaling group. |
| Health check | Allows you to customize the health check method, health check time, and health check grace period. | |
| Auto scaling policy |
| |
| Notification |
| |
| Volume | Batch operation | Manipulates volumes in bulk. |
| Volume management |
| |
| Volume snapshot |
| |
| Snapshot | Unified snapshot management | Uniformly manages VM snapshots and volume snapshots. All VM instances or volumes that have snapshots will be displayed on the snapshot management page. In addition, the VM instances or volumes can be sorted by the number of the snapshots or total capacities to improve O&M efficiencies. Doing so can help you to quickly identify snapshots that need to be cleared. |
| Batch snapshot |
| |
| Disk offering | Disk offering management |
|
| QoS setting | Allows you to set QoS for a volume by configuring the total bandwidth or read/write bandwidth when you create a disk offering. | |
| Instance offering | Instance offering management |
|
| GPU specification | GPU specification |
|
| Image management | System template | Supports system templates, including qcow2 and raw formats, and automatically matches image types. |
| ISO image | Guides a VM instance to install an operating system via an ISO image. | |
| BIOS mode |
| |
| System image uploading | Allows you to upload a system image by using a URL or a local browser. | |
| Volume image uploading | Allows you to upload a volume image by using a URL or a local browser. | |
| Image migration | Allows you to migrate images on a Ceph primary storage across multiple storage devices. | |
| ImageStore | Image storing | Stores image data, including ISO and system template. |
| Exporting image |
| |
| Obtaining existing image | When you add an ImageStore backup storage, you can obtain the existing image file under the URL of the backup storage. | |
| Image synchronization |
| |
| ImageStore cleaning | Visually cleans up the expunged invalid data in a backup storage to release storage spaces. | |
| Standard system image | Supports Windows, Red Hat, Ubuntu, and other open source Linux operating systems. | |
| Running image preset | Supports the following software operating environments:
| |
| Application image preconfiguration | Supports the following application systems:
| |
| Custom image | Allows administrators to store image files with the incremental method and realize the duplication feature intelligently by customizing images that are suitable for the operating environments of self business systems according to the standard system image and the preconfigured running image. | |
| Primary storage support | Seamlessly supports primary storages of the LocalStorage, NFS, SMP, Ceph, Shared Block types. | |
| Storage management | LocalStorage primary storage |
|
| NFS primary storage |
| |
| Shared Mount Point primary storage |
| |
| Shared Block primary storage |
| |
| Ceph primary storage |
| |
| Multiple primary storage support |
| |
| Network management | VLAN L2 isolation | Uses VLAN 802.1q for network isolation. |
| VXLAN network |
| |
| Hardware VXLAN network | Takes over SDN networks of hardware switches to the Cloud by adding SDN controller. This helps to lower network latencies and improve VXLAN network performances. | |
| Distributed flat network |
| |
| Distributed elastic network | Allows a VM instance to use a virtual network address which can map a real network. | |
| Distributed DHCP service |
| |
| Network address space reservation | Reserves network address spaces to couple with physical networks. | |
| Dynamic and static IP allocation | Not only allows you to dynamically allocate an IP address, but also allows you to specify an IP address. | |
| Multi-level network management | A VM instance can connect to multiple networks to build businesses of complex scenarios. | |
| VIP QoS setting | Limits QoS for a VIP to achieve effective allocation managements of network services. | |
| MTU | Customizes the limit of network packets. | |
| Custom gateway |
| |
| VPC vRouter |
| |
| Firewall |
| |
| VPC vRouter HA group |
| |
| VPC network |
| |
| Public network |
| |
| System network | Acts as a management network, storage network, and migration network. | |
| vRouter network |
| |
| Network diagram |
| |
| Load balancing |
| |
| Netflow |
| |
| IP statistics |
| |
| Port mirroring |
| |
| Scheduled job | Scheduled subject | Provides scheduling operations on VM instances and volumes. |
| Scheduling operations |
| |
| CloudFormation | Resource stack |
|
| Custom template | Allows you to create a resource stack template by using a designer or by uploading a local file, and to create, check, change, delete, and preview a stack template. | |
| Sample template | The resource stack template sample that is provided by the Cloud by default can be used as a reference template. | |
| Visual resource scheduling |
| |
| Security management | L3 security policy | Supports security policies based on TCP or UDP port. |
| Unified management of security group |
| |
| Performance TOP5 and performance analysis | Performance TOP5 |
|
| VM performance analysis |
| |
| Router performance analysis |
| |
| Host performance analysis | Allows you to customize data source display at different periods, and to specify a resource range. By using the filter, analyzes and sorts host CPU utilization, memory utilization, disk read speed, disk write speed, disk used capacity, disk read IOPS, disk write IOPS, disk used capacity in percent, NIC in speed, NIC out speed, NIC in packets, NIC out packets, NIC in errors, and NIC out errors. | |
| L3 network performance analysis | Allows you to customize data source display at different periods, and to specify a resource range. By using the filter, analyzes and sorts used IP count, used IP in percent, available IP count, and available IP in percent. | |
| VIP performance analysis | Allows you to customize data source display at different periods, to specify resource range, and to specify owner range. By using the filter, analyzes and sorts VIP inbound traffic in bytes, inbound traffic in packages, outbound traffic in bytes, and outbound traffic in packages. | |
| Backup storage performance analysis | Allows you to customize data source display at different periods, and to specify a resource range. By using the filter, analyzes and sorts available backup storage capacity in percent. | |
| Capacity management | Capacity management | Intuitively displays the capacity information about core resources in the Cloud.
|
| ZWatch | Host monitoring | Provides real-time monitoring of running hosts, and displays sequential diagram for monitoring CPU, memory, disk, and network. |
| VM monitoring | Provides real-time monitoring of running VM instances, and displays a sequential diagram for monitoring CPU, memory, disk, and network. | |
| Monitoring |
| |
| Alarm |
| |
| Multiple endpoints |
| |
| SNS text template | Endpoints such as email, DingTalk, Aliyun short message, and Microsoft Teams let you customize the SNS text template to facilitate your configurations as required and improve the readability of alarm messages. | |
| 3rd-party alarm message integration |
| |
| Audit | Resource audit |
|
| Operation log | Operation log |
|
| Account management | Account and user management | The account management feature includes account and user. Specifically, an account is a resource billing group, while a user can define operation permissions. |
| AD/LDAP account |
| |
| Account resource quota | Allows you to allocate the largest amount of available resources to an account in a custom manner, including the number of running VM instances, CPU, memory, volume count, total capacity of a volume, image count, total capacity of an image, and EIP count. | |
| Permission allocation of user group | Supports permission allocation of a user group to uniformly manipulate user permissions. | |
| Permission allocation of user | Allows you to allocate permissions for users. | |
| Changing VM owner | Allows you to change a VM owner and specify an account where the VM instance belongs. | |
| Changing volume owner | Allows you to change volume owner, and to specify the account where the volume belongs. | |
| Specified allocation of instance offering | Allows you to share an instance offering to others. Specifically, you can specify whether an account can use the instance offering. | |
| Specified allocation of image resource | Allows you to share an image resource. Specifically, you can specify whether an account can use the image resource. | |
| Specified allocation of disk offering | Allows you to share a disk offering. Specifically, you can specify whether an account can use the disk offering. | |
| Specified allocation of network resource | Allows you to share an L2 network resource and an L3 network resource. Specifically, you can specify whether an account can use the L2 network resource and the L3 network resource. | |
| Global settings | Allows you to directly perform global settings on various properties in the UI.
| |
| Changing password for admin account | If you forget the login password of an administrator, run zstack-ctl reset_password to restore the default setting. | |
| Billing | Custom pricing list |
|
| Billing method |
| |
| Disk performance-based pricing | Allows you to set different pricing units independently for different types of disks. | |
| Billing currency symbol | Allows you to set a billing currency symbol on the global settings. Supported currencies: CNY (¥), USD ($), EUR (€), GBP (£ ), AUD (A$), HKD (HK$), JPY ( ¥ ), CHF (CHF), and CAD (C$). | |
| Bills | Calculates and displays resource expense information of an administrator and all tenants by billing price and time of usage.
| |
| Access | TUI | Supports common O&M operations and custom OS UI. |
| GUI | Allows you to access a graphical user interface (GUI) via HTTP or HTTPS to manage the Cloud. | |
| UI language |
| |
| Login security |
| |
| Command line | Allows you to access the Cloud via command line. The command line supports full feature accesses. In addition, an account and a user can be logged in via command lines. | |
| API | Provides comprehensive APIs where APIs support Java SDK (compatibility version: Java 8), Python SDK (compatibility version: Python 2.7), and standard RESTful interface accesses. | |
| Operation assistant | Intelligent notification | Provides intelligent environment checks and operation guides for key cloud operations. |
| Affinity group | Anti-affinity group | Provides two types of affinity group strategy: anti-affinity (soft) and anti-affinity (hard) to reasonably schedule cloud resources. |
| UI augmentation | Custom product information | Allows you to customize the product logo, product name, and other information via custom UI. |
| Large-screen home page |
| |
| Encryption access | Allows you to securely log in to the Cloud via HTTPS. | |
| In-process display | Adds progress bars of multiple scenarios. | |
| VDI | Solution |
|
| UI navigation | Quick entrance | Adds a quick entrance to the product and service, and highlights important resources. |
| UI information exporting | List information exporting with CSV format | Exports VM and host main list information, making it more convenient to manage and edit parameters in list offline. |
| Tag | Resource tag |
|
| Application center | Application center | Allows you to add application plugins, such as storage, database, security, IaaS, PaaS, and SaaS. |
| AccessKey | AccessKey management | Allows you to generate an AccessKey that other clouds can call APIs. This AccessKey has the same permission as the creator who generated the AccessKey. |
| License | Cloud license (Basic License) |
|
| Module license (Plus License) |
| |
| CPU infrastructure license |
| |
| License uploading |
| |
| Management node | Multi-host management node HA |
|
| Management node |
| |
| Compute node | Batch host addition |
|
| Log server | Log server | Allows you to collect logs of a management node. You can easily collect logs of a management node to quickly locate issues and to improve O&M efficiencies of the Cloud. |
| Installation | One-click installation |
|
| Upgrade | Seamless upgrade | Allows you to seamlessly upgrade your cloud from an earlier version to a later version. |
| Incremental upgrade | Supports incremental upgrade to improve the upgrade speed greatly. | |
| Environment upgrade | Allows you to customize installation and upgrade via ZStack Expert Mode. |
| Type | Feature | Enterprise Management Module |
|---|---|---|
| Organization | User |
|
| Organization |
| |
| Role |
| |
| 3rd party authentication |
| |
| Project management | Project |
|
| project template |
| |
| project member |
| |
| Member group |
| |
| QoS setting |
| |
| Ticket management | Ticket applying |
|
| Ticket approval |
| |
| Custom process management |
| |
| Independent zone management | Platform admin |
|
| Resource isolation |
|
| Type | Feature | BareMetal Management Module |
|---|---|---|
| BareMetal management | Bare Metal cluster |
|
| Deployment server |
| |
| Bare Metal chassis |
| |
| Bare Metal instance |
|
| Type | Feature | Backup Service Module |
|---|---|---|
| Backup service | Backup |
|
| Recovery |
|
| Type | Feature | Migration Service Module |
|---|---|---|
| Migration service | V2V conversion host |
|
| V2V migration for VMware |
| |
| V2V migration for KVM |
|
| Type | Feature | Rights Separation |
|---|---|---|
| Rights Separation | Rights management | Permissions of a super admin (admin) are separated into three roles: system administrator (sysadmin), security administrator (secadmin), and security auditor (secauditor). These three roles are mutually independent and mutually balanced to further enhance the cloud security. Doing so will effectively lower the security risk that permissions of a super administrator are too large. |
| System admin | The sysadmin manages resources on the Cloud and manipulates the lifecycle of resources on the cloud excluding managements of associated permissions. | |
| Security admin | The secadmin manages cloud permissions, and allocates permissions to users or roles. | |
| Security auditor | The secauditor manages cloud auditing, and has permission controls to check and export logs that are used to audit operations of other users. |
Back to Top
Email Us
contact@zstack.ioEmail Us
contact@zstack.ioEmail Us
contact@zstack.ioThe download link is sent to your email address.
If you don't see it, check your spam folder, subscription folder, or AD folder. After receiving the email, click the URL to download the documentation.Thank you for using ZStack products and services.
Submit successfully.
We'll connect soon.Thank you for using ZStack products and services.