- Account Home
- Language
- News
- Products
-
Cases
By Service
- Help & Support
- Partners & Training
- About Us
Tenant Management allows users to create and manage their organization structures based on their actual business scenarios. It also provides features such as project-based resource access control, ticket management, and independent zone management.
The Tenant Management feature is provided in a separate module. Before you can use this feature, you need to purchase the Plus License of Tenant Management, in addition to the Base License.
 Note: Notice that project members can only view the organization structure where their team belongs to.
Note: Notice that project members can only view the organization structure where their team belongs to. Note:
Note:  Note:
Note: Active Directory (AD) is a directory service designed for Windows Standard Server, Windows Enterprise Server, and Windows Datacenter Server. AD provides an independent, standard login authentication system for increasingly diverse office applications.
AD users or organizations can be synchronized to the user list or organization of ZStack Cloud via an AD server, while specified AD login attributes can be used to directly log in to ZStack Cloud.
Lightweight Directory Access Protocol (LDAP) can provide a standard directory service that offers an independent, standard login authentication system for increasingly diverse office applications.
LDAP users can be synchronized to the user list of ZStack Cloud via an LDAP server, while specified LDAP login attributes can be used to directly log in to ZStack Cloud.
OpenID Connect (OIDC) is a set of authentication protocols based on the OAuth2 protocol, and it allows the clients to verify the user identity and obtain basic user configuration information.
The user information can be synchronized to the Cloud according to the mapping rules via an OIDC server, and users of the OIDC authentication system can log in to the Cloud without the password.
Open Authorization 2.0 (OAuth2) is a set of authorization protocol standards that can authenticate and authorize users to access related resources. The Cloud currently only supports authorization through the authorization code.
The user information can be synchronized to the Cloud according to the mapping rules via an OAuth2 server, and users of the OAuth2 authentication system can log in to the Cloud without the password.
Central Authentication Service (CAS) is a set of single sign-on protocols that allow website applications to authenticate users.
The user information can be synchronized to the Cloud according to the mapping rules via a CAS server, and users of the CAS authentication system can log in to the Cloud without the password.
The tickets created to apply for VM instances, delete VM instances, and change VM configurations will be prioritized to be submitted via the configured, custom ticket process.
 Note: The platform admin and regular platform members do not have the permission for ticket management, and the menu My Approval is not supported for these two roles.
Note: The platform admin and regular platform members do not have the permission for ticket management, and the menu My Approval is not supported for these two roles.To effectively manage the Cloud, the platform user (platform admin/regular platform member) can cooperate with the super administrator to manage and operate the Cloud together. ZStack Cloud provides various system roles such as Platform Admin Role and Dashboard Role. You can also satisfy various usage scenarios by creating custom roles at the API level.
The project management is project-oriented to plan for resources. Specifically, you can create an independent resource pool for a specific project. Project lifecycles can be managed (including determining time, quotas, and permissions) to improve cloud resource utilizations at granular, automatic level and strengthen mutual collaborations between project members.
To better provide basic resources efficiently for each project, project members (project admins, project managers, or regular project members) can submit tickets to obtain cloud resources. Tickets are reviewed and approved according to custom ticket review processes of each project. Finally, the admin, project admins, department managers, and the customized approvers approve the tickets. Currently, five types of ticket are available, including applying for VM instances, deleting VM instances, modifying VM configurations, modifying project cycles, and modifying project quotas.
Usually, a zone corresponds to an actual data center in a place. If you isolated resources for zones, you can specify the corresponding zone admins for each zone to achieve independent managements of various machine rooms. In addition, the admin can inspect and manage all zones.
The 3rd-party authentication is a third-party authentication service provided by ZStack Cloud. You are allowed to seamlessly access the third-party login authentication system. The corresponding account system can directly log in to the Cloud to conveniently use cloud resources. Currently, you can add an AD/LDAP/OIDC/OAuth2/CAS server.
By using Chrome or Firefox, go to the Account Login page via http://management_node_ip:5000/#/login. To log in to the Cloud, the admin must enter the corresponding user name and password.
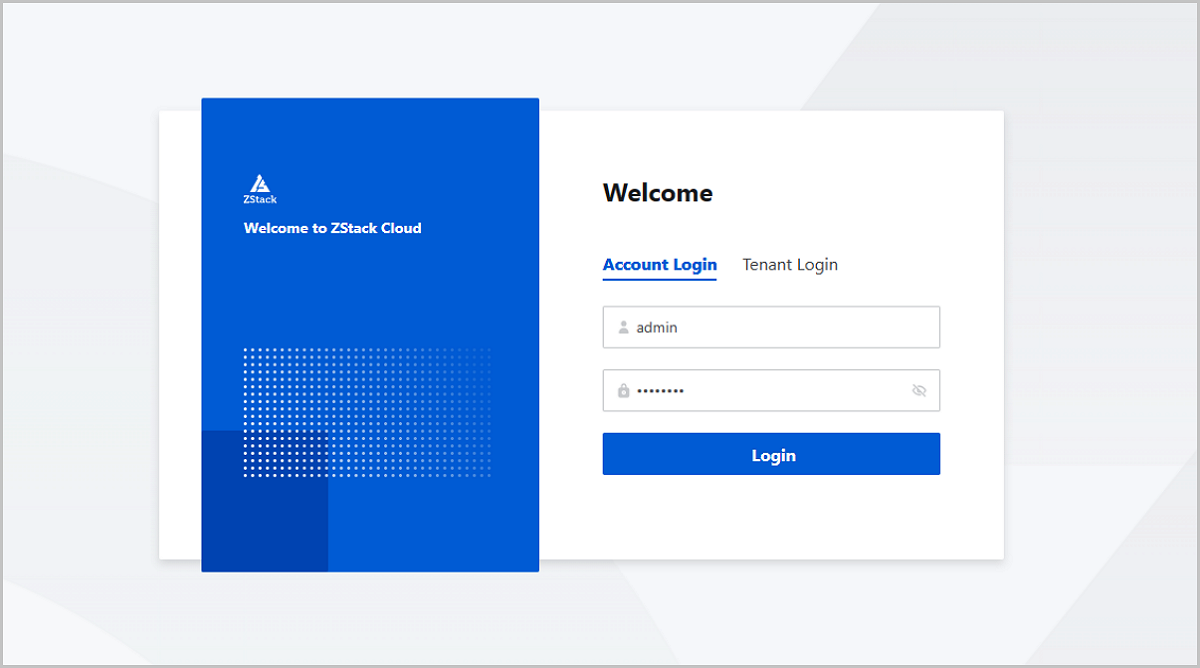
After the successful login, you can select the platform or project to be managed to log in to the corresponding management interface.
| Feature Menu | admin/Platform Admin/Regular Platform Member | Project Admin/ Project Manager | Department Manager | Regular Project Member |
|---|---|---|---|---|
| Organization | ○ | ○ | ○ | ○ |
| User | ○ | ○ | ○ | × |
| Role | ○ | ○ | ○ | ○ |
| Project Member | × | ○ | × | ○ |
| User Group | ○ | ○ | ○ | ○ |
| 3rd-Party Authentication | ○ | × | × | × |
| Project | ○ | × | ○ | × |
| Process Management | ○ | × | × | × |
| My Tickets | × | ○ | × | ○ |
| My Approval | ○ | ○ | ○ | × |
| Role | Difference |
|---|---|
| admin | A super administrator who owns all permissions. |
| Platform Admin | A platform admin is a type of administrator who has been allocated a specified zone or all zones, and assists the admin to jointly manage the Cloud. A platform admin has all the permissions that the admin has, except the following:
|
| Department Manager | The department manager is a role who has been allocated a specified department, which can be designated by the admin for the new team and responsible for managing the whole department. A department manager has the following permissions:
|
| Regular Platform Member | Platform members other than the platform admin. A Platform member has all the permission that the admin has, except the following:
|
Each organization has its own administrative departments. In a traditional IT company, resources are allocated to administrative departments based on their actual needs, and permissions are assigned as needed as well. After companies migrate their business to the cloud, they expect to enjoy the same experience in resources allocation and permissions assignment on the cloud, which is compatible with the management by administrative departments.
The Tenant Management of ZStack Cloud provides users with a range of features such as organization structure managements, project-based resource access control, ticket management, and independent zone management. Through the division of the organizational structure, it provides the same management as the administrative department and minimizes the management costs.
Back to Top
Email Us
contact@zstack.ioEmail Us
contact@zstack.ioEmail Us
contact@zstack.ioThe download link is sent to your email address.
If you don't see it, check your spam folder, subscription folder, or AD folder. After receiving the email, click the URL to download the documentation.Thank you for using ZStack products and services.
Submit successfully.
We'll connect soon.Thank you for using ZStack products and services.